Tuesday, November 3, 2020
Web Technology - Introduction
Tuesday, January 25, 2011
Distributed Denial of Service (DDoS) Attacks
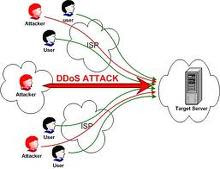 What is a Denial Of Service Attack?
What is a Denial Of Service Attack?A denial of service attack (DOS) is an attack through which a person can render a system unusable or significantly slow down the system for legitimate users by overloading the resources, so that no one can access it.
If an attacker is unable to gain access to a machine, the attacker most probably will just crash the machine to accomplish a denial of service attack,this one of the most used method for website hacking
Types of denial of service attacks
There are several general categories of DoS attacks.Popularly, the attacks are divided into three classes:
bandwidth attacks,
protocol attacks
logic attacks
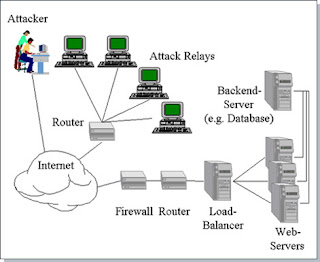
What is Distributed Denial of Service Attack?
In DDOS attack, The attacker launches the attack using several machines. In this case, an attacker breaks into several machines, or coordinates with several zombies to launch an attack against a target or network at the same time.
This makes it difficult to detect because attacks originate from several IP addresses.If a single IP address is attacking a company, it can block that address at its firewall. If it is 30000 this is extremely difficult.
Damages made By Denial of service attack:
Over past years Denial of service attack has made huge amount of damage,Many of the have been victimed of this attack
Its Real,On February 6th, 2000, Yahoo portal was shut down for 3 hours. Then retailer Buy.com Inc. (BUYX) was hit the next day, hours after going public. By that evening, eBay (EBAY), Amazon.com (AMZN), and CNN (TWX) had gone dark. And in the morning, the mayhem continued with online broker E*Trade (EGRP) and others having traffic to their sites virtually choked off.
This attack also recently hit twitter on 6th August 2009,lot of people had trouble on logging on twitter,It was brought down by denial of service attack,They tired up there server so no one can get on log on it.Websites like facebook,ebay etc have also been victim of this attack.
 Now i will show you how you can flood a website with Denial of service attack. For this tutorial we will be using one of the most effective and one of the least known tools called "Low Orbit Ion Cannon", created by Anonymous members from 4chan.org, this program is one of the best for DDoS'ing, and I have successfully used it to DDoS websites. An internet connection as bad as mine (2,500 kb/s) was able to keep a site down for a day with this program running. Remember that this tool will work best with high internet speeds, and try not to go for impossible targets (like Google, Myspace,Yahoo). LOIC is used on a single computer, but with friends it's enough to give sites a great deal of downtime.
Now i will show you how you can flood a website with Denial of service attack. For this tutorial we will be using one of the most effective and one of the least known tools called "Low Orbit Ion Cannon", created by Anonymous members from 4chan.org, this program is one of the best for DDoS'ing, and I have successfully used it to DDoS websites. An internet connection as bad as mine (2,500 kb/s) was able to keep a site down for a day with this program running. Remember that this tool will work best with high internet speeds, and try not to go for impossible targets (like Google, Myspace,Yahoo). LOIC is used on a single computer, but with friends it's enough to give sites a great deal of downtime.Prerequisites: Download LOIC (Low Orbit Ion Cannon). Open up LOIC.
(I am not giving a download link because then i will be accused for exiting hackers,try goggling).
Step 1: Type the target URL in the URL box.
Step 2: Click lock on.
Step 3: Change the threads to 9001 for maximum efficiency.
Step 4: Click the big button "IMMA FIRIN MAH LAZAR!"
Feel free to tweak around with these settings and play around with the program to get the best performance. Then minimize and go do whatever you need to do, the program will take care of the rest!
Friday, January 7, 2011
How to Test the Working of your Antivirus – EICAR Test

Have you ever wondered how to test your Antivirus software to ensure it’s proper working? Well here is a quick and easy way to test your antivirus. The process is called EICAR test which will work on any antivirus and was developed by European Institute of Computer Antivirus Research. This process can be used by people, companies and antivirus programmers to test the proper functioning of the antivirus/antimalware software without having to deal with the real computer virus which can cause damage to the computer. Here is a step-by-step procedure to test your antivirus.
1. Open a notepad (New Text Document.TXT) and copy the following code exactly onto it, and save the notepad.
EICAR Test codeX5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
2. Rename the file from New Text Document.TXT to myfile.com
3. Now run the antivirus scan on this myfile.com file.
If the antivirus is functioning properly on your computer, then it should generate a warning and immediately delete the file upon scanning. Otherwise you may have to re-install your antivirus.
You can also place the myfile.com file in a ZIP or RAR file and run a scan on it so as to ensure whether your antivirus can detect the test string in the compressed archive. Any antivirus when scanning this file will respond exactly as it will do for a genuine virus/malicious code. This test will cause no damage to your computer even though the antivirus will flag it as a malicious script. Hence it is the safest method to test the proper functioning of any antivirus.
How to Change the Logon Screen Background in Win 7

How would you like to change the logon screen background in Windows 7 so as to give your Windows a customized look and feel? With a small tweak it is possible to customize the Windows 7 logon screen and set your own picture/wallpaper as the background. Changing logon screen background in Windows 7 is as simple as changing your desktop wallpaper. Well here is a step by step instruction to customize the logon screen background.
1. The image you need to set as the background should be a .jpg file and it’s size should not exceed 245KB.
2. The image resolution can be anything of your choice. However I prefer 1440 x 900 or 1024 x 768. You can use any of the photo editing software such as Photoshop to compress and set the resolution for your image. Once you’re done, save this image as backgroundDefault.jpg.
3. You will need to copy this image to
You will need to create that path if it does not already exist on your computer.
4. Now open the Registry Editor (Start -> Run -> Type regedit) and navigate to the following key
LogonUI\Background
If Background does not exist rightclick LogonUI, select New and then Key, and then name it Background. Now locate OEMBackground (listed on the right side). If it does not exist, right-click Background and select New and then DWORD and name it OEMBackground.
5. Double-click on OEMBackground and set the Value Data to 1.
6. Now log-off to see the new logon screen background. If you would like to revert back to the default background, just set the Value Data back to 0.
I hope you like this trick. Just try out and give your feedback!
Chat without Yahoo Messenger or Gtalk
Moreover if the matter is highly confidential, then it is necessary to have a totally private chat where the messages are exchanged only between the people involved in the chat and not with any other third party servers. At these situations, it is better to chat without Yahoo messenger.
So, how to carry out a private chat without Yahoo messenger or Gtalk?
For this purpose there exists many softwares that support’s you to host a web-based chat system without any additional software or services. So with these softwares the exchange of messages takes place directly between the two persons engaging in the chat and will not pass through any other third party server. This ensures 100% privacy and eliminates the desperate need to chat with Yahoo messenger.
One of my favorite program for private chat is Easy Chat Server
Easy Chat Server is a Windows program that allows you to host a web-based chat system without any additional software or services. Unlike other chat server, you do not need to install Java. It allows you to build one or more web-based chat rooms on your machine, and provides advanced chat functionalities aiming to offer discussion space for your users, customers and partners.
Here are some of the screenshots of Easy Chat Server.
Key Features of Easy Chat Server:
- Easy to use, Simple installation that will have you up and running in minutes.
- 128-Bit Security Socket Layer(SSL) support. Support for server level certificate creation.
- Instantly runs a complete chat server on your PCs – does not need to install any Web Server.
- Supports full private messaging and One to One private chat.
- Support of images, smileys, avatar icons.
- Full chat and access logs are available within the chat server.
- Have a built-in IP Filter, supports banning/unbanning IP address, securely.
- Multiple styles available for the user to customize rooms.
- Unlimited rooms and users, no any annual, per-user, or maintenance fees.
- No spyware, adware or other unwanted extra programs.
How to track the original location of an email via its IP address
There are basically two steps involved in the process of tracking an email: find the IP address in the email header section and then look up the location of the IP address.
Finding the IP address of an email sender in GMail,
Yahoo Mail, and Outlook
Let’s go ahead and take a look at how you would do this for G
oogle, Yahoo and Outlook since those are the most popular email clients.
Google’s Gmail
1. Log into your account and open the email in question.
2. Click on the down arrow that’s to the right of th
e Reply link. Choose Show Original from the list.
Now here’s the technical part that I was telling you about earlier! You need to look for the lines of text that start with “Received: from“. It might be easier to simply press Cntrl + F and perform a search for that phase. You’ll notice that there are several Received From’s in the message header. This is because the message header contains the I
P addresses of all of servers involved in routing that email to you.
To find the first computer that originally sent the email, you’ll have to find the Rece
ived From that’s farthest DOWN. As you can see from the above image, the first one is from a computer called “aseem” with the IP address 72.204.154.191.
Then it was routed to my ISP’s server at eastrmmtao104.cox.net and so on and so forth till it got to your email server.
The computer aseem is my personal home computer and that’s my p
ublic IP address for my house! I’ll go through Yahoo and Outlook before
talking
about tracking the location of that IP address.
Yahoo Mail Beta
1. Log into your account and open the email (if you’re using Yahoo Mail Beta with th
e new preview interface, make sure you double-click on the email so tha
t it opens in a new tab)
2. At the top right, you’ll see there is a drop-down option w
here Standard Header is selected by default.
3. Click on it and choose Full Header.
Again, you’ll see the same information as before, just in a different window:
1. Open the email in Outlook by double-clicking on it
2. Go to View at the top menu (the menu options for the email, not the main Outlook window) and choose Options.
You’ll get a dialog box where you can set the message options and at the bottom you’ll see the Headers box. For some silly reason, the box is very small and you have to scroll a lot, so it’s best to simply copy and paste the text into Notepad to view it more easily.
Tracking the location of an IP address
Now that we have our originating IP address of 72.204.154.191, let’s fi
nd out where that is! You can do this by perform a location lookup on the IP ad
dress. My favorites are IP2Location and GeoBytes IP Locator.
GeoBytes gave me a big map of New Orleans, LA along with a bunch of other information about the location itself.
IP2Location also gave me the same information pretty much, including the ISP (Cox Communications). Of course, this is correct since I live in New Orleans!
If you want more information, you can do a WHOIS database search also. My favorite one is the ARIN WHOIS Database Search. This will give you information on who hosts that IP address and their registration information. You can always contact them to try and find more information on that particular IP address.
Have fun tracking down those emails!
Thursday, April 15, 2010
What to do when your Orkut Account is Hacked ?
It can be a nightmare if someone else takes control of your Google Account because all your Google services like Gmail, Orkut, Google Calendar, Blogger, AdSense, Google Docs and even Google Checkout are tied to the same account.
Here are some options suggested by Google Support when your forget the Gmail password or if someone else takes ownership of your Google Account and changes the password:
1. Reset Your Google Account Password:
Type the email address associated with your Google Account or Gmail user name at google.com/accounts/ForgotPasswd – you will receive an email at your secondary email address with a link to reset your Google Account Password. This will not work if the other person has changed your secondary email address or if you no longer have access to that address.
2. For Google Accounts Associated with Gmail:
If you have problems while logging into your Gmail account, you can consider contacting Google by filling this form. It however requires you to remember the exact date when you created that Gmail account.
3. For Hijacked Google Accounts Not Linked to Gmail:
If your Google Account doesn’t use a Gmail address, contact Google by filling this form. This approach may help bring back your Google Account if you religiously preserve all your old emails. You will be required to know the exact creation date of your Google Account plus a copy of that original “Google Email Verification” message.It may be slightly tough to get your Google Account back but definitely not impossible if you have the relevant information in your secondary email mailbox.










